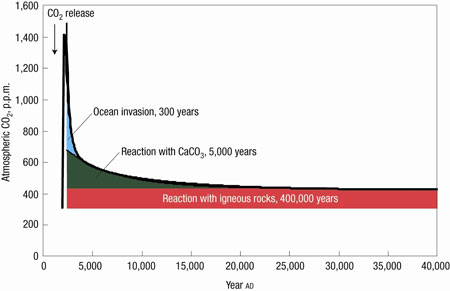
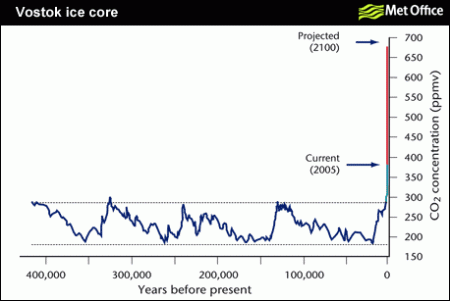
The above, famously, is Google’s motto. When I first saw it, it seemed like an embodiment of the ways in which Google differs from other large corporations. They are involved in charitable works, in areas including infectious disease and renewable energy. Furthermore, they give away most of their products, getting the financing from those famous automatic ads.
On further reflection, however, “Don’t be evil” isn’t some lofty, laudible goal we should applaud Google for having. Rather, it is the absolute minimum required of them, given just how much of our personal information they have acquired. Think about GMail: many of us have tens of thousands of messages, many of them highly personal, entrusted unencrypted to Google’s servers. If they were evil – or even a few of their employees were – they could embarass or blackmail an enormous number of people. What Google has is, in many cases, far more intimate than what sites like Facebook do. Facebook may have some private messages to your friends, but Google is likely to have financial information, medical test results, photos you would never put on Facebook, etc.
Now, Google has incorporated a very useful phone calling system into GMail. Install a plugin, and you can make free calls to anywhere in Canada and the United States. In my limited experience, it seems to work better than SkypeOut, while being free to boot. Of course, it is another example where we really need to trust Google to behave ethically. For Google Voice, they already developed algorithms to convert spoken words into transcribed text. Users of their phone service need to trust that their conversations are not being archived or – if they are – that the transcripts will not be used in any nefarious ways.
In short, Google must avoid being evil not out of benevolence, but because their whole business model requires people to view them that way. So far, their products have been remarkably empowering for a huge number of people (any other sort of email seems deeply inferior, after using GMail). If they are going to maintian the trust of users, however, they are going to need to avoid privacy disasters, or at least keep them on a pretty minor scale, like when Google Buzz abruptly let all your friends know who else you are in contact with.